Wireless Security
In WLANs, privacy is achieved by data contents protection with encryption. Encryption is optional in 802.11 WLANs, but without it, any other standard wireless device,
can read all traffic in network. There have been three major generations of security approaches, which is mentioned below:
a) WEP (Wired Equivalent Privacy)
b) WPA (Wi-Fa Protected Access)
c) WPA2/802.11i (Wi-Fa Protection Access, Version 2)
Each of these protocols has two generations named as personal and enterprise template.
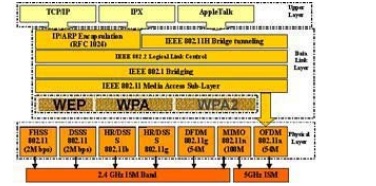
802.11 OSI Model
There are many versions of 802.11 a,b,g ,n & i released.The 802.11i security standard which was released in June 2004 is supposed to be the final solution to wireless security issue.
It improves
a) authentication,
b) integrity and
c) data transfer.
Due to the market need of a better substitute to WEP vendors (WiFi Alliance) took a subset of it and market the new product before the final release under the name WPA (WiFi Protected Access), which was released in April 2003. After the final release of 802.11i the vendors implemented the full specifications under the name WPA2. 802.11i supports two methods of authentication. The first method is using 802.1x and EAP to authenticate users. For users who can not or do not want to implement the first method, another method was proposed to use per-session key per-device. This method is implemented by having a shared key (like the one in WEP) called GMK (Group Master Key), which represent the base key to derive the other .
GMK is used to derive PTK (Pair Transient Key) and PSK (Pair Session Key) to do the authentication and data encryption.To solve the integrity problem with WEP, a new algorithm named Michael is used to calculate an 8-byte integrity check called MIC (Message Integrity Code). Michael differs from the old CRC method by protecting both data and the header. Michael implements a frame counter which helps to protect against replay attack. To improve data transfer, 802.11i specifies three protocols: TKIP, CCMP and WRAP.
TKIP (Temporal Key Integrity Management) was introduced as a "band-aid" solution to WEP problems. One of the major advantages of implementing TKIP is that you do not need to update the hardware of the devices to run it. Simple firmware/software upgrade is enough.Unlike WEP, TKIP provides per-packet key mixing, a message integrity check and a re-keying mechanism . TKIP ensures that every data packet is sent with its own unique encryption key. TKIP is included in 802.11i mainly for backward compatibility.
WRAP (Wireless Robust Authenticated Protocol) is the LAN implementation of the AES encryption standard.It was ported to wireless to get the benefits of AES encryption. WRAP has intellectual property issues, where three parties have filed for its patent. This problem caused IEEE to replace it with CCMP.
CCMP (Counter with Cipher Block Chaining Message Authentication Code Protocol) is considered the optimal solution for secure data transfer under 802.11i. CCMP uses AES for encryption.