Security Architecture
RISK = (Threats x Vulnerabilities ) / ( Countermeasures ) x Assets.
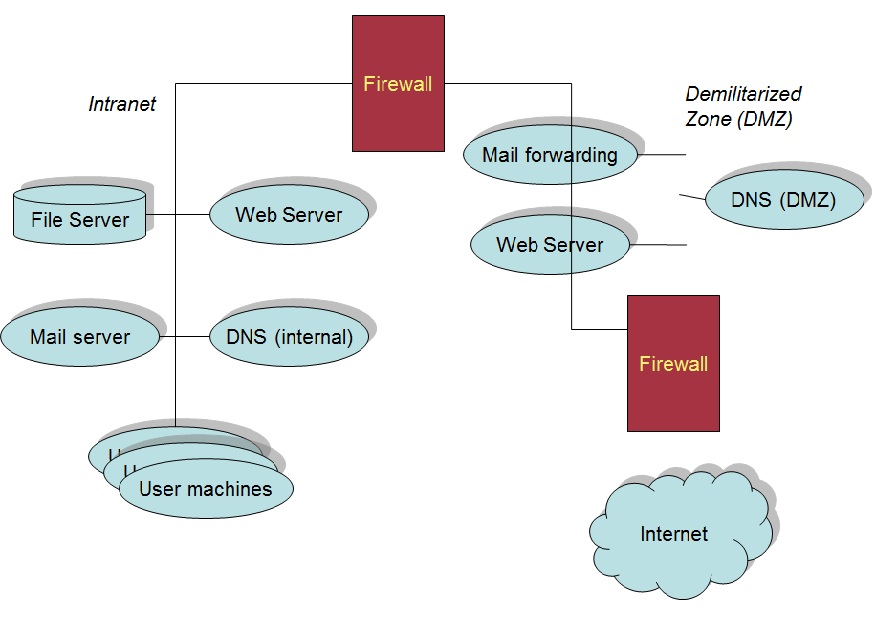
a) Global Information Assurance Certification(GIAC) Security Architecture.

A complete diagram of GIAC’s security architecture including all public and non rout-able (RFC 1918) private IP addressing is provided in the above diagram.The security architecture consists of concentric systems arranged to help provide "defense-in depth" of GIAC’s three critical Databases. The core systems employed to protect
GIAC’s network from unauthorized access consist of the following:
1. A Border Router (or "External Router” or "Filtering Router”)
2. A Primary Firewall (or "External Firewall”), which also provides VPN services
3. A Secondary Firewall (or "Internal Firewall”)
These devices form concentric rings around GIAC’s network that provide three lines of defense between the Internet and GIAC’s most critical assets, the Databases that house all company information.
b) Typical Corporate network