Top 3 Hash algorithms
1) BLAKE
2) Gr
ø
stl3) JH
BLAKE:
BLAKE is a family of four hash functions: BLAKE-224, BLAKE-256, BLAKE-384, and BLAKE-512 . As SHA-2, BLAKE has a 32-bit version (BLAKE-256) and a 64-bit one (BLAKE-512), from which other instances are derived using different initial values, different padding, and truncated output.
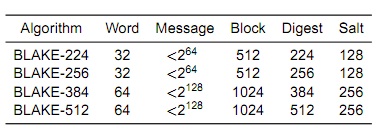
Sizes in bits
The BLAKE hash functions follow the HAIFA(a general iteration mode for hash functions) the compression function depends on a salt 1 and the number of bits hashed so far (counter), to compress each message block with a distinct function. The structure of BLAKE’s compression function is inherited from LAKE : a large inner state is initialized from the initial value, the salt, and the counter. Then it is injectively updated by message-dependent rounds, and it is finally compressed to return the next chain value. This strategy was called local wide-pipe in , and is inspired by the wide-pipe iteration mode. Initialization rounds finalization chain value salt counter message salt chain value next chain value . The inner state of the compression function is represented as a 4×4 matrix of words. A round of BLAKE-256 is a modified "double-round” of the stream cipher ChaCha: first, all four columns are updated independently, and thereafter four disjoint diagonals. In the update of each column or diagonal, two message words are input according to a round-dependent permutation. Each round is parametrized by distinct constants to minimize self-similarity. After the sequence of rounds, the state is reduced to half its length with feedforward of the initial value and the salt. An implementation of BLAKE requires low resources, and is fast in both software and hardware environments. In 180 nm ASIC, BLAKE-256 can be implemented with about 13 500 gates, and can reach a throughput of more than 4 Gbps; BLAKE-512 can be implemented with about X Y gates, and can reach a throughput of more than 6 Gbps.
Gr
ø
stl: Grøstl is an iterated hash function with a compression
function built from two fixed, large, distinct permutations. The design of Grøstl is transparent
and based on principles different from those used in the SHA-family.
The two permutations are constructed using the trail design strategy, which makes
it possible to less vulnerable or not vulnerable to
cryptanalytic attacks.
Grøstl is a byte-oriented SP-network which borrows components from the AES. The S-box
used is identical to the one used in the block cipher AES and the diffusion layers are constructed
in a similar manner to those of the AES. As a consequence there is a strong confusion and
diffusion in Grøstl.
Grøstl is a so-called wide-pipe construction where the size of the internal state is signifi
cantly larger than the size of the output. This has the effect that all known, generic attacks on
the hash function are made much more difficult.
Grøstl has counter-measures against
side-channel attacks which is based on AES.
JH:
JH has four versions of hash algorithms – JH-224, JH-256, JH-384,
and JH-51.
Hash function JH consists of five steps:
a) Padding the message M
b) Parsing the padded message into message blocks
c) Setting the
initial hash value H(0)
d) Computing the final hash value H(N)
e) Generating the message digest by truncating H(N)
The memory required for the hardware implementation of JH hash functions is 1536 bits (including the 512-bit message block). With 256 additional memory bits, the round constants of JH can be generated on the fly. JH-224, JH-256, JH-384 and JH-512 share the same compression function. JH is strong in security. Each message block is 64 bytes. A message block passes through the 42-round compression function that involves 10752 4×4-bit Sboxes. In the differential trail compression function involved more than 700 active Sboxes. The large number of active Sboxes ensures that JH is strong against differential attack.